The cybersecurity landscape is a constantly evolving battleground, with new threats and vulnerabilities emerging almost daily. As we look to the future, it's clear that a revolution is on the horizon, promising to reshape how we protect our digital world. This revolution won't be a single, sudden event, but rather a confluence of technological advancements, shifting paradigms, and a renewed focus on proactive defense.
The Current State of Affairs: A Reactive Stance
For too long, cybersecurity has been primarily reactive. Organizations invest heavily in firewalls, intrusion detection systems, and antivirus software, essentially building digital walls to keep attackers out. When a breach inevitably occurs, the focus shifts to incident response: identifying the extent of the damage, patching vulnerabilities, and attempting to recover. This approach, while necessary, is akin to constantly repairing a leaky roof instead of building a stronger one in the first place.
The sheer volume and sophistication of modern attacks are overwhelming this reactive model. We're seeing an increase in state-sponsored attacks, highly organized criminal enterprises, and even individual hackers leveraging advanced tools and techniques. Traditional security measures are struggling to keep pace, leading to widespread data breaches, financial losses, and erosion of trust.
Pillars of the Revolution
The upcoming revolution in cybersecurity will be built upon several key pillars, each contributing to a more proactive, intelligent, and resilient defense.
1. Artificial Intelligence and Machine Learning: The Brains of the Operation
One of the most significant game-changers will be the widespread adoption and integration of Artificial Intelligence (AI) and Machine Learning (ML). These technologies will move beyond simple anomaly detection to predictive threat intelligence and autonomous response.
Predictive Analytics: AI will analyze vast datasets of threat intelligence, network traffic, and user behavior to identify patterns and predict potential attacks before they even materialize. Imagine a system that can flag a suspicious email campaign hours before it hits your employees' inboxes, based on its similarity to past phishing attempts and the sender's unusual activity.
Autonomous Threat Hunting : Instead of security analysts manually searching for threats, AI-powered systems will autonomously hunt for vulnerabilities, misconfigurations, and malicious activity across entire networks. They will be able to correlate seemingly disparate events, uncovering complex attack chains that would otherwise go unnoticed.
Self-Healing Networks : In the most advanced scenarios, AI will enable "self-healing" networks. When a threat is detected, the system will not only isolate the compromised segment but also automatically reconfigure network policies, patch vulnerabilities, and deploy countermeasures without human intervention.
2. Zero Trust Architecture: Trust No One, Verify Everything
The traditional "castle-and-moat" security model assumes that once inside the network perimeter, everything can be trusted. The Zero Trust model completely upends this notion. It operates on the principle of "never trust, always verify," regardless of whether the user or device is inside or outside the network.
Granular Access Control : Every access request, whether from an employee, a partner, or an IoT device, is rigorously authenticated and authorized. Access is granted based on a least-privilege principle, meaning users and devices only have access to the resources absolutely necessary for their function.
Continuous Verification : Trust is not a one-time event. User identities, device posture, and application behavior are continuously monitored and re-verified. If any anomaly is detected—such as a user accessing unusual files or a device showing signs of compromise—access can be immediately revoked or escalated for further scrutiny.
Micro-segmentation : Networks are divided into small, isolated segments. This limits the lateral movement of attackers even if they manage to breach one segment, preventing them from accessing the entire network.
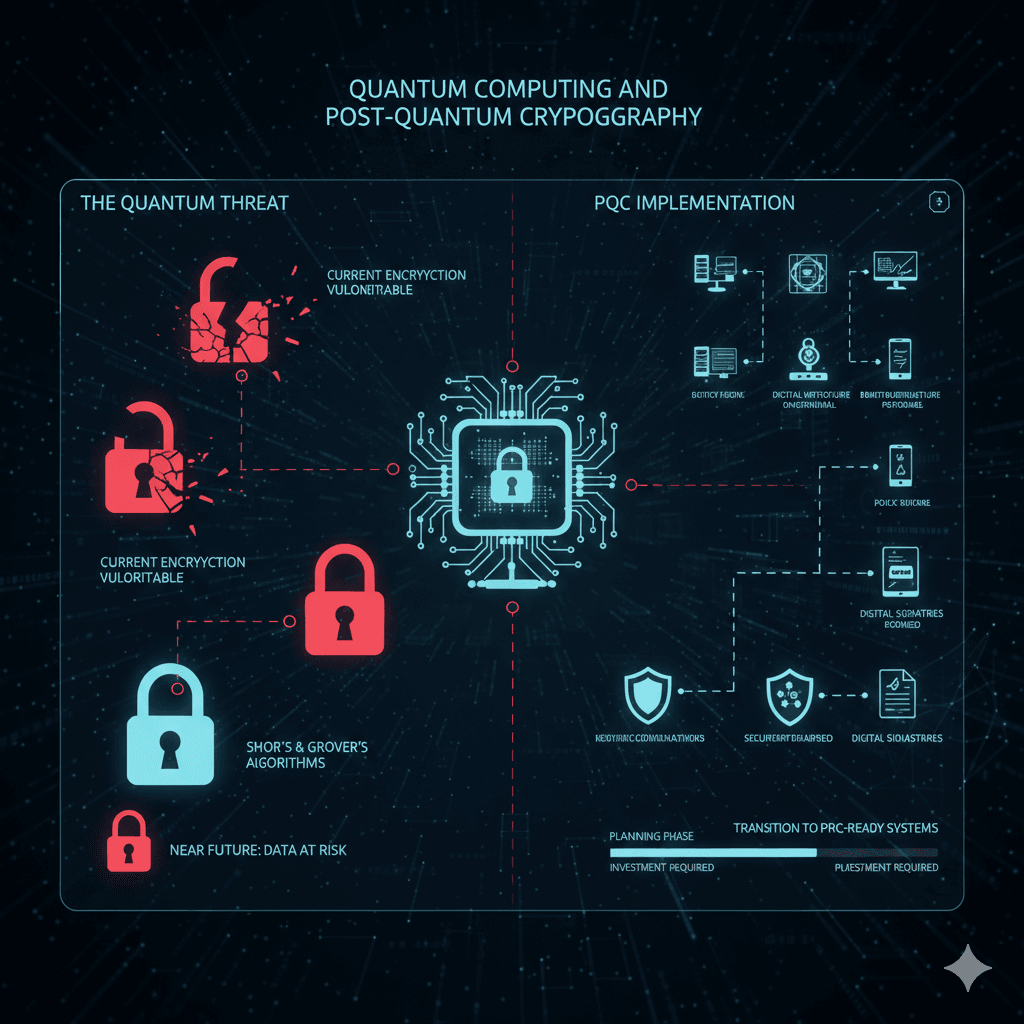
3. Quantum Computing and Post-Quantum Cryptography: The Encryption Frontier
While quantum computing promises unprecedented computational power, it also poses a significant threat to current encryption standards. Many of the cryptographic algorithms that secure our online communications and data today could be easily broken by a sufficiently powerful quantum computer.
The Quantum Threat : This isn't a problem for tomorrow; it's a concern for the near future. As quantum computers become more sophisticated, the race is on to develop "post-quantum cryptography" (PQC) – new cryptographic algorithms that are resistant to attacks from both classical and quantum computers.
PQC Implementation : The transition to PQC will be a monumental undertaking, requiring a complete overhaul of our digital infrastructure. This includes everything from secure communication protocols and digital signatures to data encryption and key exchange mechanisms. Organizations will need to start planning and investing in PQC-ready systems to safeguard their data against future quantum threats.